Introducing the World’s Only Smart ECDN
Introducing the World’s Only Smart ECDN
Machine learning is revolutionizing modern business, improving efficiency while decreasing costs and increasing profits. According to a 2021 McKinsey survey , 56% of organizations today are using machine learning in at least one business function. In the same study, 27% of respondents attributed at least 5% of their earnings before interest and taxes (EBIT) to AI and machine learning.
At Kollective, we understand the power machine learning offers businesses, which is why we developed the world’s first and only Smart ECDN. In this article, we explore the specifics of our new intelligent solution and detail how simple managing your network has become.
What is Kollective’s Smart ECDN?
Kollective’s Smart ECDN was developed for one purpose – to radically simplify ECDN onboarding and management so that your network – consistently achieves peak performance. There’s not just one feature that makes this possible, but instead, a suite of intelligent solutions that work harmoniously to make the world’s first and only Smart ECDN. Five core features define Kollective’s Smart ECDN:
- Easy Activation
- Self-Service Network Topology Management
- Network Modeling
- Anomaly Detection
- Suggestive Analytics
Stress-Free Onboarding
Abstracting difficulty out of complex situations is a core function of a “smart” system. Kollective’s new onboarding wizard achieves this in spades, providing a fast and stress-free process for clients to configure their setup in five simple steps:
- Create an Account – Log in and authenticate with your Microsoft or G-Suite account.
- Configure Integrations – Select your integrations from an extensive list of the world’s leading front-end video applications and Kollective’s tool will walk you through how to quickly configure each to work with our ECDN.
- Define Network Configurations – While Kollective has terrific out-of-the-box settings that work well for most networks, our wizard allows users to customize their network settings quickly.
- Manage Privacy Settings – Enable custom privacy settings to control what data is collected.
- Invite Users & Complete Setup
Self-Service Network Topology Management
Whether your business is large or small, you understand that networks are complex. That is why Kollective has revolutionized how clients view and manage global network settings. Users can import all their network locations into our system to create self-service delivery parameters and unique network policies and behaviors for each.
With Kollective’s Smart ECDN, controlling your network has never been easier. Have offices in the DACH region that require different security settings than your offices in the Americas? Navigate to the “Network Locations” tab in the “Network Settings and Configuration” dashboard and create a unique policy for those locations.
Network Modeling
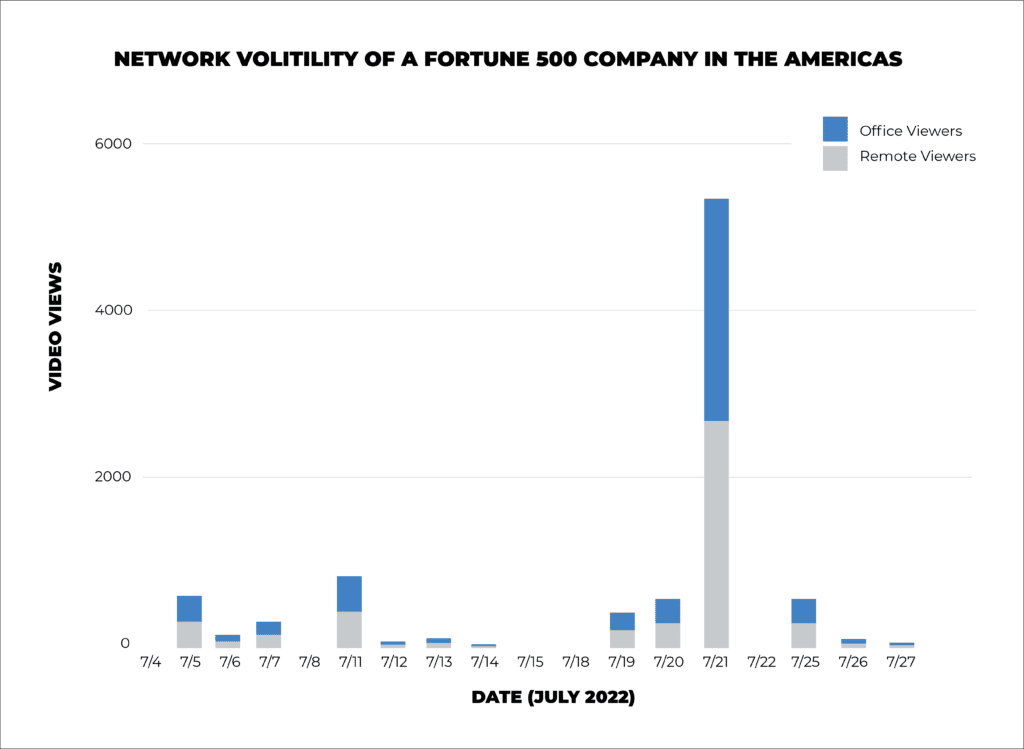
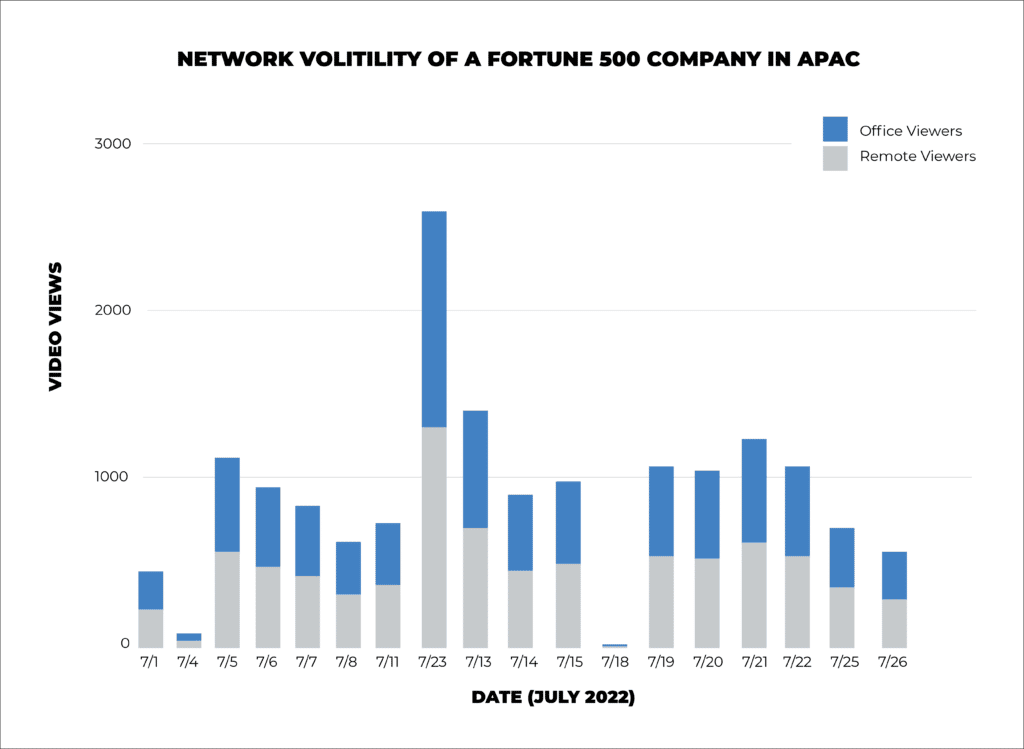
With any investment your business makes, it is crucial to understand the value you receive in return. That is why Kollective developed the Rapid Network Test (RNT) – to allow businesses to simulate how Kollective performs when networks experience a high volume of concurrent video streams.
While the RNT reveals if your network is ready to peer, Kollective’s Smart ECDN ensures that your network performs at its peak efficiency by running silent tests that construct a detailed model of your optimal network, providing the data it needs e to improve continuously. With Kollective’s Smart ECDN, you don’t need to be an IT expert to configure your network to stream flawless live videos. Model your network before running your first event and stream with confidence.
Smart Diagnostics
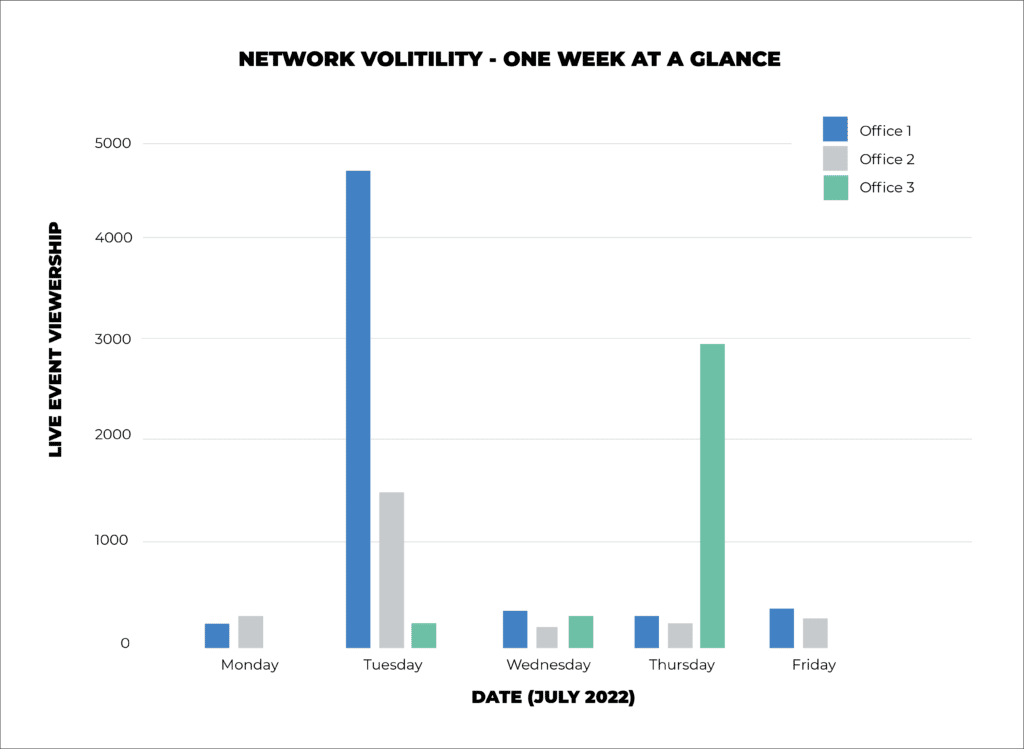
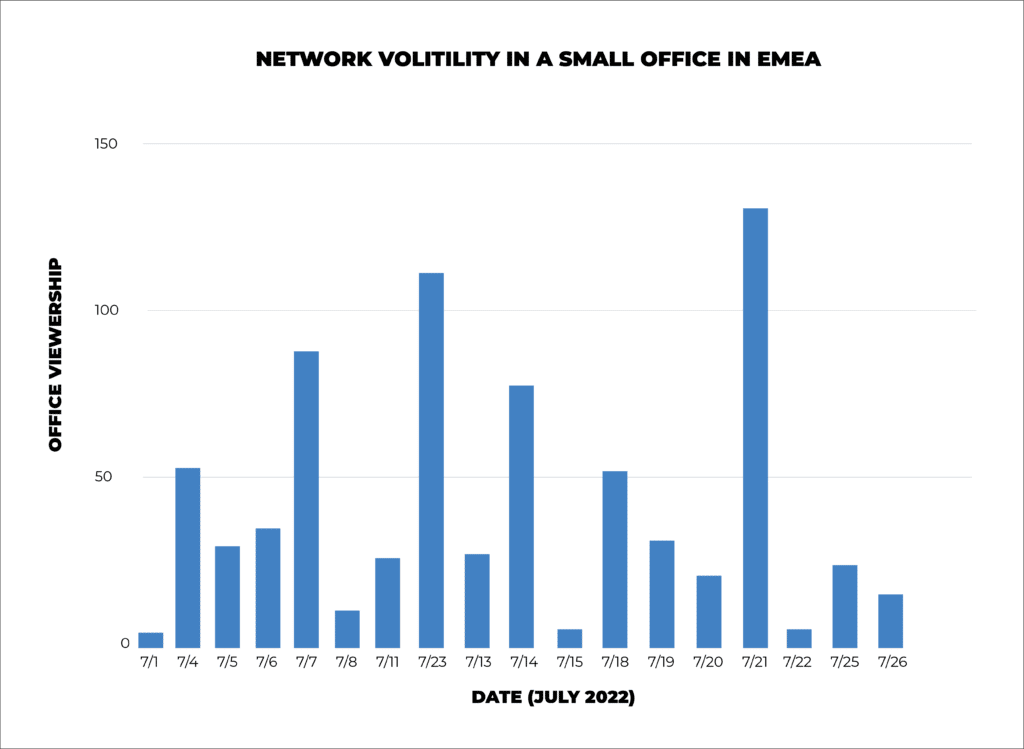
While Kollective’s network modeling optimizes your network before an event, our diagnostic dashboards provide ongoing support to identify and resolve issues as they arise. Our smart ECDN achieves this by using anomaly detection and machine learning to surface insights from past events to make future ones perform better.
Kollective’s solution delivers excellent results out-of-the-box, but we do not settle anything but the best. Our intelligent diagnostics stems from our broader philosophy to constantly refine and improve our processes to deliver the best product on the market. By detecting anomalies in your network through our diagnostics dashboard, Kollective’s Smart ECDN ensures that your network will be ready to meet the challenges as your business continues to evolve and grow.
What is Anomaly Detection?
One of the most powerful factors of Kollective’s smart diagnostics is its ability to recognize anomalies in your network. Our machine-learning protocols examine patterns of data playback that meet certain expectations. When something unexpected happens on your network, our anomaly detection algorithms recognize aberrant behavior based on indicators versus normal behavior and flag the event. These reports are the final pillar of our Smart ECDN, suggestive analytics.
Suggestive Analytics
When an event is flagged for aberrant behavior in Kollective’s smart diagnostics dashboard, our system analyzes the precise cause. It then alerts you to where the problem occurred in your network, what users were affected, and how to solve it so it does not happen again. Below are a few examples of problems that might occur and how quickly Kollective’s Smart ECDN will identify and solve them through the power of automation.
- Bitrate Thrash – One locality is having a poor event because too many bitrates were requested (e.g. 10). Kollective’s system would flag the event in the diagnostics dashboard, identifying that location with the recommendation that bitrate is pinned on that area of your network.
- Excessive Stalling – One locality is experiencing lengthy buffering during an event because peering nodes are stalling. Kollective would flag this event, and our suggestive analytics would recommend adjusting the performance settings in that location to “peering,” so more segments of a stream are built up before the video is peered to others on the node.
Experience the World’s Only Smart ECDN
Machine learning and AI adoption continue to climb as businesses steadily uncover their potential. Kollective’s Smart ECDN is our first step into this realm as we continue to seek new and innovative ways to create the best possible experience for our customers. Try Kollective today and experience the power of the only ECDN that constantly optimizes your network for peak performance.
The post Introducing the World’s Only Smart ECDN appeared first on Kollective Technology .