What the SolarWinds Hack Taught Us About the Need for Endpoint Security Reporting & Software Delivery Analytics
By now, almost everyone has heard of the disastrous SolarWinds hack . To re-cap, in March 2020, hackers stealthily installed malware into SolarWinds Orion, a network-monitoring software used for IT infrastructure management. This allowed the hackers to gain access to highly sensitive data via a covertly inserted backdoor. The attack went undetected for months and was first publicly reported in December 2020 after being spotted by cybersecurity firm FireEye. Over a period of eight months, at least 24 organizations installed the SolarWinds software laced with malicious code, including various federal, state and local governments and private sector companies.
When Microsoft found out they were among those compromised in the hack, they made quick work to remove the digital certificates that the Trojaned files used, announced that it was updating Microsoft Windows Defender, moved to a sinkhole domain and changed Windows Defender’s default action for Solorigate from “Alert” to “Quarantine.” Microsoft’s quick actions lead to neutralizing and killing the malware while gaining control over the malware’s infrastructure from the attackers.
The SolarWinds hack highlights the devastating impact of software supply chain attacks and underscores the fact that most organizations are unprepared to prevent and detect such threats. When a security breach happens, speed is a critical factor in remediation, but you also need granular insights into software delivery to understand overall system health.
Best Practices to Avoid and Respond to a Cyber Security Attack
According to a Cisco report , “Major incidents and losses can be avoided by proactively refreshing the technology used and by learning from prior incidents, through prompt disaster recovery, sufficient security tech, timely incident response and accurate threat detection.”
You can help defend your company from a cyber-attack by conducting risk assessments, mitigating against risks that cannot be removed, preparing and implementing a breach response plan and implementing cyber security best practices. In addition to scanning your systems on a continuous basis, Gurpreet Dhillon, Ph.D of Virginia Commonwealth University , recommends organizations to:
- Install sensors or mechanisms to collect potential hazards
- Conduct automatic searches at regular intervals for potential flaws
- Collect results from different divisions and/or stakeholder groups
- Triage and analyze results on an ongoing basis
- Fix the most critical issues first and develop a priority list
- Report progress and continuously improve
If your organization falls victim to a cyber-attack despite all of the security measures you’ve taken to prevent it, after you discover the breach:
- Survey: Identify the attacker and find out where the attacker entered
- Limit: Filter traffic and isolate system
- Record: Find effects and identify disruptions
- Engage: Connect with District Attorney and engage with FBI Infragard
- Notify: Notify affected persons and seek legal counsel
- Learn: Document learning points and proactively ensure learning moving forward
Even when taking the upmost security measures, a data breach can happen to any organization. Reduce your risk of a cyber-attack by implementing and following your organization’s best practices, and if a breach does occur, follow your security response plan.
Managing Network Health via Security Analytics
Security reporting leverages a combination of software, algorithms and analytics processes to detect potential threats to IT systems, not just sniff out hacks as they occur.
“Many organizations do not use security analytics to its full capabilities; often the analysis is relegated simply to identifying network attacks. However, this is only one subset of the types of security analytics that should be deployed. Security analytics provides insights into how well security programs are working. It can also help identify problem areas and can warn of imminent or active attacks” says privacy and security expert Rebecca Herold .
Ian McClarty, President of PhoenixNAP Global IT Services , elaborates, “Analytics are key to security. As the complexity of IT networks has grown, the inventiveness and sophistication of cyber security threats and attacks has grown just as quickly.”
Endpoint analytics can also give clues to security breakdowns and help identify policies or hardware issues that may be slowing down devices, so you can proactively make changes without disrupting end users.
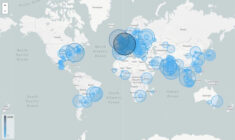
Paired together, security reporting and endpoint analytics can help an IT department understand the data flowing in– to and out of its network, detect potential threats and monitor user experience and hardware. The safety of an organization’s data and IT systems increasingly depends on having an effective, real-time monitoring security and endpoint analytics solution.
Kollective for Software Delivery Accelerates Patching & Provides Insight into System Health with Intelligent Analytics Reporting
According to IBM Cost of a Data Breach Report 2020 , the average cost of a corporate data breach is $3,860,000. Extensive cloud migrations are the number one cause of data breach, with 24% occurring at the end point, 19% due to a system misconfiguration and 16% because of a vulnerability in third-party software. To help avoid a costly breach, increase your endpoint security by reducing network risk with Kollective for Software Delivery .
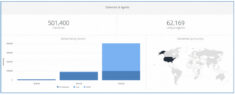
Kollective helps minimize the risk of data breach by ensuring 100% delivery of software updates and security patches when distributing content via Microsoft System Center Configuration Manager (SCCM). By leveraging the scale and flexibility of the cloud, Kollective optimizes software updates and patch delivery to minimize downloads and vulnerabilities with faster and more reliable patch distribution.
Kollective’s solution delivers:
- 70% faster software deployment
- No impact to network bandwidth
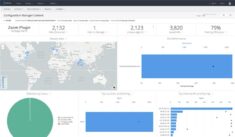
- Analytics that provide a full view of your network
Want to make your SCCM more powerful? Kollective IQ is an advanced analytics platform that gives you deeper insight into all your endpoints. It allows you to easily create dashboards and reports, providing the metrics your organization needs to better understand network performance and verify the success of deliveries.
With Kollective for Software Delivery you can achieve greater than 95% peering efficiency, and significantly reduce your Wide Area Network (WAN) bandwidth utilization. This means faster and more reliable delivery of ConfigMgr content to the edge of your network. Kollective IQ provides the analytics you need to ensure your network environment is secure and fully optimized.
To learn more about Kollective for Software Delivery, request to speak with an expert today.
The post What the SolarWinds Hack Taught Us About the Need for Endpoint Security Reporting & Software Delivery Analytics appeared first on Kollective Technology .